Cowpatty 2 0 Windows 10
CoWPAtty is a C-based tool for running a brute-force dictionary attack against WPA-PSK and audit pre-shared WPA keys. If you are auditing WPA-PSK networks, you can use this tool to identify weak passphrases that were used to generate the PMK. Supply a libpcap capture file that includes the 4-way.
Bond shine youtube. Bond also performed '' alongside at the 2012 Olympics Closing Ceremony. They returned to the Olympic Stadium in London in July 2013 to perform at The National Lottery Anniversary Run event. According to the band's webpage, the group recorded a medley of Lady Gaga hits at the request of its Japanese label. The Lady Gaga medley was available initially by phone download and was released digitally, soon after, as part of a special Japanese album release.
As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords, coWPAtty. In this tutorial, we’ll use the piece of software developed by wireless security researcher Joshua Wright (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords.
It is easier than you think, so let’s get to it! Step 1: Find the Cowpatty Cowpatty is one of the hundreds of pieces of software that are included in the BackTrack [] and Kali [] OS’s. If you are using a different Distro, you can download and install. For this demo, I will be using BackTrack. For some reason in BackTrack, it was not placed in the /pentest/wireless directory, but instead was left in the /usr/local/bin directory, so let’s navigate there.
Cd /usr/local/bin Because cowpatty is in the /usr/local/bin directory and this directory should be in your PATH, we should be able to run it from any directory in BackTrack. Step 2: Find the Cowpatty Help Screen To get a brief rundown of the cowpatty options, simply type: cowpatty BackTrack will provide you a brief help screen. Take a note that cowpatty requires all of the following: • a word list • a file where the password hash has been captured • the SSID of the target AP Step 3: Find the AP Just as in cracking with aircrack-ng, we need to put the wireless adapter into monitor mode. Airmon-ng start wlan0 Now, look at the available APs using the monitor interface and airodump: airodump-ng mon0 leave this screen by hitting CTRL+C Step 4: Start a Capture File Next, we need to start a capture file where the hashed password will be stored when we capture the 4-way handshake.
If you do not have Windows Embedded CE 6.0 R2, you can also download an evaluation copy from the Microsoft Download Center.There're different types of maps for the Car GPS navigation. The most common ones are Sygic, igo, tomto, Garmin, ect. We would like to show you a description here but the site won’t allow us. Sygic Sygic McGuider World Maps 2009 v7.71 Sygic for windows installed laptop MapMyIndia 7.0 Premium *2012* with Sygic Aura Win CE 6 (Maybe other Our supported Windows platform are WindowsCE, Windows Mobile, WindowsXP and Windows 8, and the installation procedure is the same for all of them. 31 Jul 2016 Results 1 - 20 Sygic 12.1.0 Wince Code 31. Sygic maps windows ce download free. Free download sygic map software for windows ce Files at Software Informer. Sygic Assistant is a very useful tool. Map of Europe is a Worldwide Background Map for GPS.

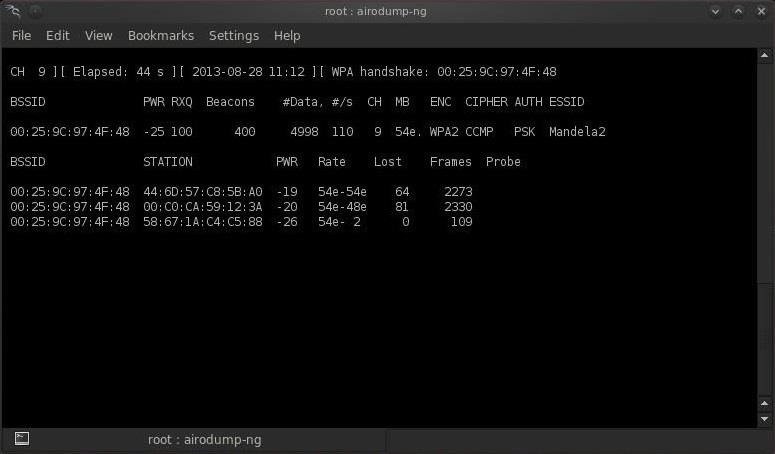
Airodump-ng –bssid 00:25:9C:97:4F:48 -c 9 -w cowcrack mon0 This will start a dump on the selected AP (00:25:9C:97:4F:48), on the selected channel (-c 9) and save the the hash in a file named cowcrack. Step 5: Capture the Handshake Now when someone connects to the AP, we’ll capture the hash and airdump-ng will show us it has been captured in the upper right-hand corner. Some people just wait for a computer to connect. Other people send DEAUTH packets to kick them off the wifi, and then they automatically connect again, at which time you will capture the handshake. I may cover this tomorrow or the next day.
Step 6: Run the Cowpatty Now that we have the hash of the password, we can use it with cowpatty and our wordlist to crack the hash. Cowpatty -f /pentest/passwords/wordlists/darkc0de.lst -r /root/cowcrack-01.cap -s Mandela2 As you can see in the screenshot above, cowpatty is generating a hash of every word on our wordlist with the SSID as a seed and comparing it to the captured hash. When the hashes match, it dsplays the password of the AP.